Protect
Gain control and peace of mind with the PC-DMIS Protect permissions manager
Ready to get started?
Talk to an expert and discover what Hexagon can do for your organization.
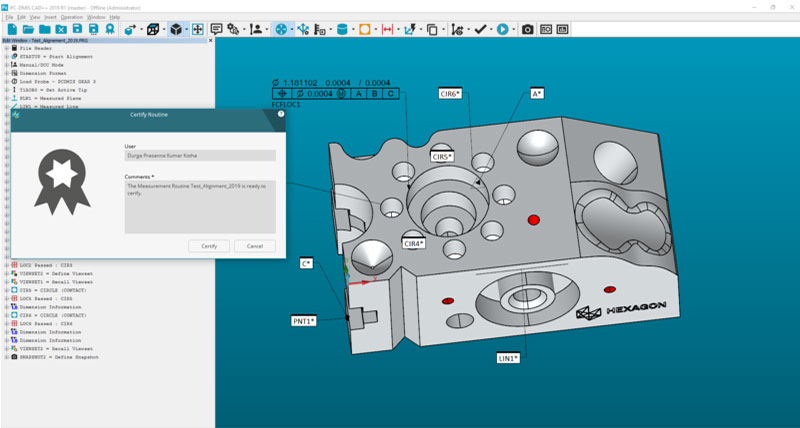
Measurement routines are valuable data files. It is important that any changes are controlled and tracked in order to ensure repeatable and reliable metrology operations, and therefore consistently high quality products. This is important in all processes, and in some industries – such as medical, food and aerospace – the need for tight process control and accreditation is paramount.
Protect uses the permissions given to PC-DMIS users to control access to measurement routines and track modifications to these ‘protected’ files. All changes are tracked and a report can be generated, making Protect ideal for any business that needs to meet specific industry standards or process controls.
Protect is a cost option feature for PC-DMIS that means once a measurement routine is approved, the file is ‘certified’. Once it is certified, only specific PC-DMIS account holders can make changes, and any changes are recorded, logged and can be traced back to a user and time for future audits.
This added level of control and protection can help manufacturers work towards process compliance, and may support customers in their accreditations or certifications according to specific standards such as:
Protect uses the permissions given to PC-DMIS users to control access to measurement routines and track modifications to these ‘protected’ files. All changes are tracked and a report can be generated, making Protect ideal for any business that needs to meet specific industry standards or process controls.
Protect is a cost option feature for PC-DMIS that means once a measurement routine is approved, the file is ‘certified’. Once it is certified, only specific PC-DMIS account holders can make changes, and any changes are recorded, logged and can be traced back to a user and time for future audits.
This added level of control and protection can help manufacturers work towards process compliance, and may support customers in their accreditations or certifications according to specific standards such as:
- FDA (Food and Drug Administration CFR 21 Part 11)
- ISO 13485 for medical and health sector
- IATF 16949 (Clause 8.5.2 Identification and Traceability) for automotive industry
- Specific Federal Aviation Administration traceability requirements for aeronautics or other specific traceability requirements
-
Features & BenefitsPDF export of change log
Once changes have been made and recorded in the Protect log, the user can create and export a PDF file of the changes for auditing records or management reporting.
Critical information logged
Only a user with the correct access rights can make changes to a program. When a change is made, key information is recorded in the log including: the name of the user, the actual change made, the time and date of the change and a reason or comment for the change.
Simple control of Protect privileges
Only your identified and approved users can edit protected files. Any user without Protect privileges can open or run a protected file but will be unable to edit it. Users can be easily added or removed from the appropriate user group.
HxGN LIVE Global
Learn how our technologies can digitally transform facilities, assets and workflows to drive productivity.